By Sam Rinko
AI security software provides businesses with advanced toolsets to combat the ever-persistent threat of cyberattack. From identifying suspicious patterns to proactive threat hunting, AI security solutions offer a proactive and intelligent defense mechanism against malicious attacks that goes beyond traditional cybersecurity solutions.
We evaluated leading AI security solutions to see how they compared on features, pricing, and use cases. Here are our picks for the best AI security tools for your business in 2024:
- Darktrace: Best for Neutralizing Novel Threats
- Crowdstrike: Best for Monitoring User Endpoint Behavior
- SentinelOne: Best for Advanced Threat Hunting
- Check Point: Best for Network Monitoring and Security
- Fortinet: Best for Preventing Zero-Day Threats
- Zscaler: Best for Data Loss Prevention
- Trellix: Best for Environments Requiring Constant Monitoring
- Vectra AI: Best for Hybrid Attack Detection and Response
- Cybereason: Best for Defending Against MalOps
- Tessian: Best for Protecting Against Email-Based Threats
Top AI Security Software
The chart below shows at a glance how the leading AI security software compares on use case, complexity, and starting price, followed by detailed reviews of the systems.
| Best For | Complexity | Starting Price | |
|---|---|---|---|
| Darktrace | Neutralizing novel threats | High | $30,000 |
| Crowdstrike | Monitoring user endpoint behavior | High | $299.95 per year |
| SentinelOne | Advanced threat-hunting and incident response capabilities | Low | $69.99 per endpoint |
| Check Point | Network monitoring and security | High | Available upon request |
| Fortinet | Preventing zero-day threats | High | Available upon request |
| Zscaler | Data loss prevention | Moderate | Available upon request |
| Trellix | Complex IT environments that require continuous monitoring | High | Available upon request |
| Vectra AI | Hybrid attack detection, investigation, and response | Moderate | $4 per month per IP |
| Cybereason | Defending against MalOps | High | Available upon request |
| Tessian | Protecting against email-based threats | High | $40,080 per year |
TABLE OF CONTENTS
Featured Partners: Cybersecurity Software
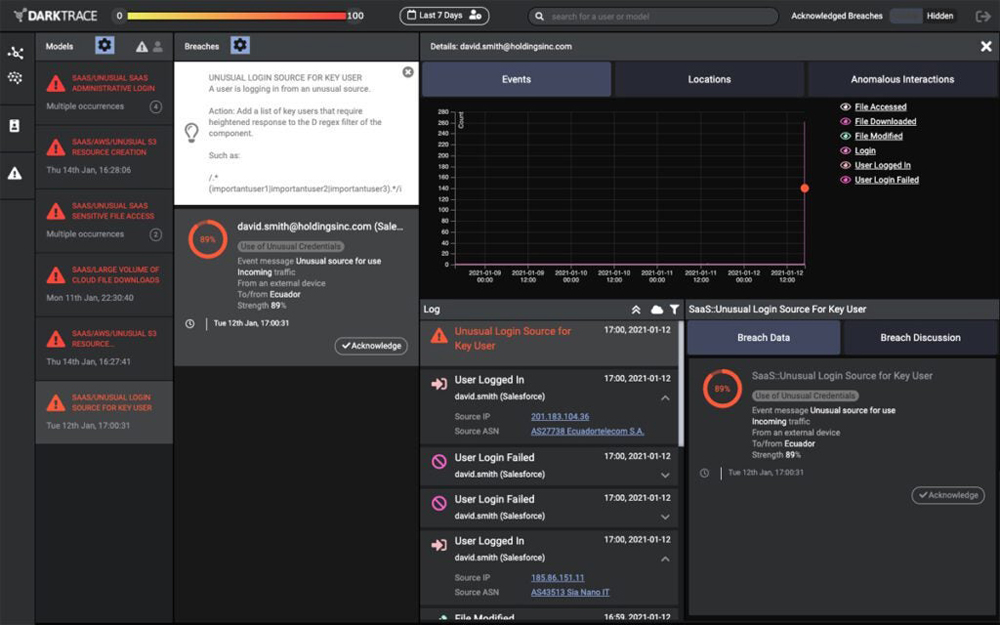
Darktrace
Best for Handling Novel Threats
Darktrace’s cyber AI platform uses AI and machine learning algorithms to identify and respond to cyberthreats in real time. The AI security software offers a unified solution that provides protection across the cloud, SaaS, email, IoT, ICS, remote endpoints, and the network.
Predictive in its approach, Darktrace’s self-learning AI technology is designed to understand and adapt to the unique patterns of a company’s network by learning from users and devices as well as the connections between them, allowing it to detect anomalous, novel behavior that may indicate a cyberattack.
Darktrace’s AI algorithms also constantly learn and adapt to the evolving threat landscape, enabling it to identify known and unknown threats and detect abnormal activity that may indicate the presence of previously unseen threats. To that end, Darktrace is geared to combat LOTL (living off the land) attacks, highly targeted attacks, and AI attacks.
In reviewing the tool, I was pleased to see that the platform offers a wide range of AI-supported services like AI-based attack simulation. This enables teams to prepare for and test out strategies against attacks in a real-world setting. I also liked how it offers a robust AI incident investigation and reporting feature to help you learn why attacks occurred and how to work to make sure they never happen again.
Pros and Cons
| Pros | Cons |
|---|---|
| Hardens defenses | Expensive, especially for small businesses |
| Provides instant attack visibility | Complex initial setup |
Pricing
Darktrace doesn’t advertise its product pricing on its website; publicly available data cites a 30-day free trial and the following pricing:
- Small Bandwidth: $30,000 for up to 300 Mbps of average bandwidth and 200 hosts
- Medium Bandwidth: $60,000 for up to 2 Gbps of average bandwidth and 1,000 hosts
- Large Bandwidth: $100,000 for up to 5 Gbps of average bandwidth and 10,000 hosts
Features
- Darktrace PREVENT continuously monitors your attack surface for risks
- Darktrace DETECT offers instant visibility of threats
- Darktrace RESPOND interrupts fast-moving attacks
- Darktrace HEAL restores your system back to health after an attack
For a deeper understanding of cybersecurity and AI, read our guide to Generative AI and Cybersecurity.
![]()
CrowdStrike
Best for Monitoring User Endpoint Behavior
CrowdStrike Falcon is an AI-native security solution that leverages machine learning in security and behavioral AI. Its custom large language model works to protect endpoints, detect threats, and respond to security incidents in real-time.
Ideal for endpoint protection, this AI security software consolidates next-generation antivirus (AV), endpoint detection and response (EDR), and a 24/7 managed threat hunting service into a single lightweight agent, providing organizations with complete visibility and protection across their endpoints.
The lightweight agent continuously monitors and protects endpoints against various attacks using real-time indicators of attack and threat intelligence from across the enterprise, thereby providing proactive threat-hunting capabilities. CrowdStrike uses behavioral AI to detect anomalies in user endpoint behavior. This means it can monitor current activity as compared with past user actions to protect the perimeter. Its models are trained on trillions of data points daily, allowing it to target threats ahead of time.
In comparing CrowdStrike to competitors like Darktrace, I found it to be best-suited for mid-to-large enterprises that want a comprehensive solution that works across almost all areas of cybersecurity, with an emphasis on endpoint protection.
Pros and Cons
| Pros | Cons |
|---|---|
| Provides visibility across devices, accounts, and cloud workloads | User interface could be improved |
| Can stop identity-based attacks in real-time | Learning curve to get familiar with the platform’s capabilities |
Pricing
- Falcon Go: $299.95 per year
- Falcon Pro: $499.95 per year
- Falcon Enterprise: $924.95 per year
- Falcon Elite: Custom pricing
- Falcon Complete MDR: Pricing available upon request
Features
- Unified attack surface visibility
- Pre- and post-incident response services
- Can import IOCs
- An AI-based detection system called user and entity behavior analytics (UEBA)
![]()
SentinelOne
Best for Advanced Threat Hunting
SentinelOne’s AI-backed cybersecurity solution, SentinelOne Singularity, is an autonomous security platform that combines an endpoint protection platform (EPP), EDR, and extended detection and response (XDR) into a single unified platform.
The platform uses AI and ML algorithms to provide real-time prevention, detection, and threat hunting across user endpoints, containers, cloud workloads, and IoT devices. It protects against a wide array of advanced cyberthreats, including malware, ransomware, exploits, and fileless attacks.
What I found most noteworthy is the platform’s powerful automated incident response capabilities, which enable security teams to quickly stop and recover from security breaches and other attacks, thus mitigating the damage. For example, if a threat is detected, the tool will automatically trigger the correct incident response workflows. Examples include blocking suspect traffic or isolating attacked endpoints.
I scored SentinelOne’s Singularity as one of the best AI security software tools because it aims to simplify and strengthen enterprise security operations by providing comprehensive and automated protection across the entire threat lifecycle, from pre-execution to post-execution.
Pros and Cons
| Pros | Cons |
|---|---|
| Provides quality threat-hunting tools and insights | Digital forensics and incident response only available to enterprise users |
| 24/7/365 threat hunting and managed services | Reporting capability could be better |
Pricing
- Singularity Core: $69.99 per endpoint
- Singularity Control: $79.99 per endpoint
- Singularity Complete: $159.99 per endpoint
- Singularity Commercial: $209.99 per endpoint
- Singularity Enterprise: Pricing available upon request
Features
- Ability to identify and triage threats
- Can ingest data from many sources
- Will identify and quickly launch threat detection and response
- Advanced threat-hunting capabilities
- Automated incident response workflows
![]()
Check Point Software
Best for Network Monitoring and Security
Check Point Software Technologies uses AI capabilities to enhance its cybersecurity offerings at various levels. Its AI security software, ThreatCloud AI, acts as the brain of its security solutions, driving the actions and collecting and analyzing threat data from various sources.
This AI intelligence also supports Check Point’s global sensors, research teams, customers, and partner community. This intelligence is then integrated into Check Point’s security solutions to protect against known and unknown threats; the AI enables the response to be proactive.
One of Check Point’s top features is Quantum, which is designed to maximize protection of your network. It leverages AI-powered security gateways to block against zero-day attacks like phishing, malware, and DNS attacks. I was impressed to see that the block rate was an industry-leading 99.8 percent for malware and 100 percent for phishing.
As for threat prevention solutions, it offers security features such as a firewall, intrusion prevention system (IPS), anti-bot, antivirus, application control, and URL filtering to enable you to combat cyberattacks and threats.
One thing I found particularly valuable for busy, overwhelmed security professionals was how Check Point enables users to manage access controls across all networks from one smart console. This is a highly efficient approach.
Pros and Cons
| Pros | Cons |
|---|---|
| XDR/XPR aggregates incidents | Can be expensive, especially for smaller businesses |
| Improves accuracy with AI engines aggregator and machine-validated signature system | Steep learning curve |
Pricing
- Contact for a detailed quote
Features
- Will block zero-day attacks across networks, endpoints, and cloud
- Uses UEBA to identify anomalous behavior indicative
- Third-party threat intelligence feeds
- ThreatCloud AI campaign threat hunting
- Anti-phishing AI engine
![]()
Fortinet
Best for Preventing Zero-Day Threats
Fortinet FortiGuard is an AI security software incorporating threat intelligence, real-time threat analysis, and global threat protection to identify and block advanced threats and attacks. The services integrate with security solutions across Fortinet’s broad portfolio to provide security capabilities that protect applications, web traffic, content, devices, and users located anywhere.
In comparing Fortinet to other AI cybersecurity solutions, I found its key differentiator to be its ability to prevent zero-day threats. Always learning, the AI-based threat detection software is regularly updated with the latest threat intelligence from FortiGuard Labs experts, data from across Fortinet’s broad sensor base, and zero-day intelligence feeds. This ensures that organizations are protected against emerging threats and zero-day vulnerabilities.
Additionally, FortiGuard’s service portfolio includes content security and NOC/SOC security; this is very important given the core nature of the Security Operations Center. It also offers SOC-as-a-Service functionality and provides consistent cybersecurity assessments and readiness alerts.
Pros and Cons
| Pros | Cons |
|---|---|
| Protect against network- and file-based threats | Steep learning curve |
| Security profile customization | Customer support could be better |
Pricing
- Contact for a detailed quote
Features
- Guards against all OWASP Top-10 threats, DDOS attacks, and bot attacks
- Detects compromised systems
- AI-based inline malware prevention
- AI-powered SandBox engine
- Focuses on preventing zero-day threats
![]()
Zscaler
Best for Data Loss Prevention
Zscaler is a cloud-based AI security software that provides internet security and web filtering services. It uses proprietary large language models and AI to enhance and improve its security offerings.
The company’s LLMs are integrated with a massive data lake that handles more than 300 billion daily transactions, allowing for continuous learning and improvement of its AI models. This enables Zscaler to provide advanced AI-driven outcomes and capabilities for IT and security teams. These AI-driven outcomes are particularly notable for data loss prevention; Zscaler’s common DLP use cases include securing data in motion, securing endpoint data, and the ability to protect against misconfigurations.
Additionally, its AI-powered security tools also provide tremendous control over generative AI tools by giving you visibility into user input prompts and the power to quickly isolate apps. This is important in an age when companies increasingly train generative AI tools on sensitive company data.
On another note, I like how Zscaler’s deep focus on Zero Trust connectivity. Zero Trust assumes everything on the network is potentially malicious and does not automatically trust any user or device. Instead, it authenticates and validates every user and device before granting access to resources, which also supports DLP. This allows it to protect against even the most inconspicuous of attacks.
Pros and Cons
| Pros | Cons |
|---|---|
| AI-powered browser isolation | Customer support could be improved |
| Dynamic, risk-based policy | Requires fast internet service to function well |
Pricing
- Contact for a detailed quote
Features
- AI-powered phishing and C2 detection
- Standard digital experience monitoring
- Data loss prevention capability
- AI-powered phishing detection
- Automated, AI-powered root cause analysis
![]()
Trellix
Best for Environments that Require Continuous Monitoring
Trellix is a result of the merger of the security product divisions of McAfee Enterprise and FireEye. This AI security software excels in continuous monitoring, which enables proactive threat detection by combining signature-based identification, behavioral analytics, and real-time monitoring.
Its open, comprehensive XDR platform, Trellix XDR, uses advanced machine learning and AI techniques to analyze, correlate, and monitor data from various sources, including network traffic, endpoint behavior and threat intelligence feeds. Its continuous monitoring enables it to detect sophisticated and complex threats that traditional security solutions might miss.
I especially like how Trellix’s AI is capable of operationalizing threat intelligence. It can reduce alert noise and automate responses to security incidents, thus resulting in faster response times, better block rates, and mitigated damage. Notably, its XConsole combines security controls and an advanced research center to provide a unified view of the security landscape and enhanced visibility into network traffic, endpoint activity, and user behavior, allowing analysts to identify and remediate threats before they can cause damage.
Pros and Cons
| Pros | Cons |
|---|---|
| Integrates with more than 1,000 third-party sources | Complex initial setup |
| Comprehensive on-premises product portfolio | The user interface can be better |
Pricing
- Contact for a detailed quote
Features
- Signature-based engine to find and block known malware
- Behavior-based analytics engine to stop advanced threats
- UEBA capability to detect anomalous user behaviors
- Real-time monitoring
![]()
Vectra AI
Best for Hybrid Attack Detection and Response
Vectra AI Attack Signal Intelligence platform combines human intelligence, data science, and machine learning to detect–and respond to-cyberattacks in real time. The company’s AI and cybersecurity solution gives you constant visibility into your network security posture, helping you prioritize potential threats and enabling both quick response and mitigation to minimize the impact of hybrid cyberattacks.
Significantly, with the prevalence of these “hybrid attacks”—two or more combined attacks to break the perimeter—Vectra focuses on preventing them in particular. Using contextual insights, AI-driven detections, and third-party automated responses, the AI security software combats various hybrid attack types, such as account takeovers, data breaches, ransomware, supply chain attacks, and even nation state attacks.
A feature I found notable is how, unlike other tools, Vectra AI puts an emphasis on showing you which threats are most critical, and then triaging irrelevant anomalies to reduce alert noise that inevitably wastes your team’s time.
Pros and Cons
| Pros | Cons |
|---|---|
| Attack prioritization | Reporting capability can be improved |
| AI-driven insights | Product documentation can be improved |
Pricing
Vectra AI doesn’t display product pricing on its website. Publicly available information shows pricing ranges as follows:
- Up to $5,000 for month-to-month licenses
- Up to $50,000 for annual licenses, depending on your selected service
- For actual rates, contact Vectra’s sales team for a quote
Features
- Analyzes attacker behaviors post-compromise and in real time
- Correlates and ranks incidents by urgency across environments
- Threat intelligence integration
- AI-based threat detection and response geared for hybrid attack defense
- Machine learning techniques, along with deep learning and neural networks
![]()
Cybereason
Best for Defending Against MalOps
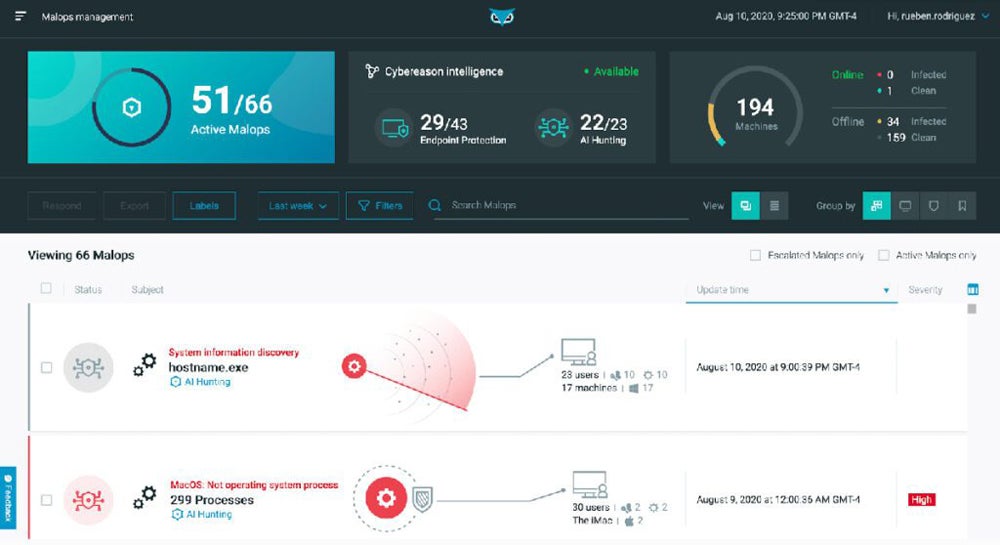
Cybereason is an AI security software that uses behavioral analytics and artificial intelligence to detect and respond to threats in real-time, helping organizations recognize and stop attacks before they can cause significant damage. In comparing it to other AI security tools, I was impressed that Cybereason’s platform specializes in combating MalOps, which is the full narrative of events in coordinated hacking attacks.
To accomplish this, the solution uses NGAV-based behavioral and machine learning techniques, with an approach that works to prevent known and unknown MalOps threats for fast response across the network and cloud infrastructure. Cybereason also uses an AI-driven XDR platform. As security professionals know, XDR architecture is considered to be leading-edge in the security sector.
These XDR tools facilitate forensic analysis that helps security teams as they investigate and remediate security incidents in rapid-response mode. In other words, it provides intelligence that helps your team to outsmart the attackers.
Pros and Cons
| Pros | Cons |
|---|---|
| Automatic prediction and response to mitigate attacks | Steep learning curve |
| Quality customer support | Lacks some reporting capabilities |
Pricing
- Contact the company for a detailed quote
Features
- Posture and incident management
- Threat intelligence
- Mobile threat defense
- Digital forensic and incident response
![]()
Tessian
Best for Protecting Against Email-Based Threats
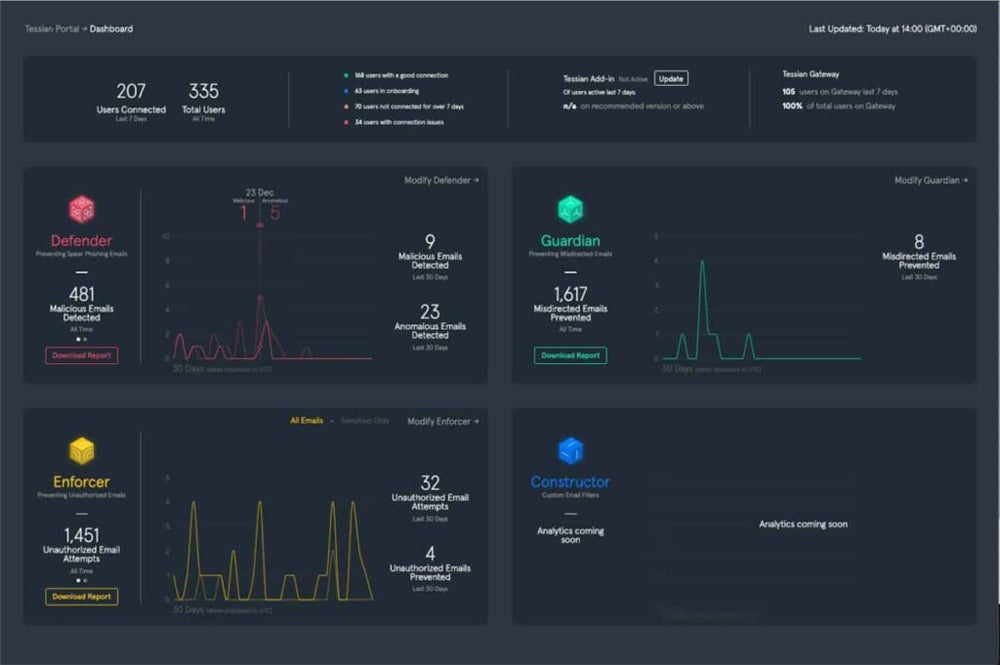
Tessian’s platform uses AI behavior-based protection to prevent accidental and intentional loss of data over email. This is a vitally important goal, given that email is one of the true weak points in the perimeter and one of the most widely used tools for businesses.
Tessian protects organizations from phishing attacks, accidental data leakage, and unauthorized email activity. To do so, it uses AI algorithms to analyze email communication patterns, identify anomalies and suspicious behavior, and provide real-time warnings and training to employees regarding potential security risks.
I found the AI security coaching to be a distinct and helpful feature, as it takes this burden off of cybersecurity professionals to monitor and coach users on security decisions. The AI automatically gives users contextual alerts to help them make smart security decisions in the moment and sharpen their sensitivity to threats over time.
Significantly, Tessian is also capable of protecting companies against compromised business email, account takeover and “misdirected” email. Additionally, it offers tools to combat image and QR code attacks, attack types that are likely to grow in the years ahead. Overall, Tessian is a great tool for making your email communication more secure and preventing data breaches caused by human error or malicious intent.
Pros and Cons
| Pros | Cons |
|---|---|
| Hunt, investigate, and respond to email threats quickly | Steep learning curve |
| Perform threat network analysis | Users report occasional false positives |
Pricing
- Tessian doesn’t advertise product pricing
- According to public data, the platform costs $40,080 per year for 100 inboxes
- Contact for a detailed quote
Features
- Protect against QR code phishing, BEC, executive impersonation, and domain spoofing
- Automates removal of end user reported threats
- Behavioral analysis
- Identifies threats in image-based text, QR codes, URLs, and email
Honorable Mentions: Leading AI Security Solutions
Based on our product research and evaluation, here are the other top-tier platforms that fell just short of our list but are still worth recommending:
- Cylance: Using AI and ML to detect and prevent malware, Cylance AI offers protection for modern enterprise infrastructure, legacy devices and isolated endpoints.
- Deep Instinct: Uses a prevention-first approach to stop ransomware and other malware by using predictive prevention powered by deep learning.
- LogRhythm: A security intelligence company that offers various cybersecurity solutions, including SIEM, SOAR, UEBA and NDR to help organizations detect, investigate and respond to cyberattacks.
- VIPRE: Offers two threat intelligence solutions (VIPRE ThreatAnalyzer and VIPRE ThreatIQ) designed to detect, analyze and destroy persistent threats.
- Stellar Cyber: An AI-driven open XDR platform that collects and normalizes security alerts, logs and telemetry from products. It also automatically detects and correlates threats using purpose-built Graph ML, allowing you to hunt for, investigate and eliminate threats quickly.
- Sophos: Offers detection and response, firewall, cloud and managed service solutions for network security and unified threat management.
- Dataminr: Features real-time event and risk detection to help you discover, prioritize and categorize critical information. The solution uses deep learning-based multi-modal AI fusion methods to improve event detection accuracy.
- Cynet: Built on an automated XDR platform that allows security teams to detect, prevent, correlate, investigate and respond to threats across endpoints, users, networks and SaaS applications.
- SparkCognition: Offers AI solutions that enable companies to predict future outcomes, optimize processes and prevent cyberattacks.
- Symantec Targeted Attack Analytics: Identifying incidents with AI and advanced machine learning, Symantec EDR uses TAA data to generate new incidents or to add to existing Symantec EDR incidents.
How We Evaluated the Best AI Security Software
There are many factors that determine the best AI security solution, including security needs, organization size, team, and budget. While most AI security software promises similar capabilities, they are not created equal—some are more powerful than others, with cutting edge XDR capability, while some excel in certain areas like predictive threat response.
For instance, Tessian caters to those shopping for email security, while Check Point is more focused on network security. Vectra includes tools to prevent hybrid attacks.
We considered how the systems met typical business requirements in a range of areas, including price, ease of use, sophistication, features, and pros and cons. Based on those findings, we identified the best use cases for each of the systems on our list.
How to Choose the Best AI Security Software for Your Business
Review your current security architecture and determine which areas most need AI-powered solutions. This may include email security, network security, endpoint protection, data loss prevention, or insider threat detection. Be sure to consider costs, features, complexity, and integrations before settling for a solution. To the extent possible, use a trial version of the AI cybersecurity solution before making a final decision.
Frequently Asked Questions (FAQs)
We answered the most commonly asked questions about the best AI security solutions to help you determine the best option for your business.
What is the Best AI Security Solution?
The best AI security tool for you depends on your needs. Our analysis above evaluated several top-rated AI security solutions for different users. The best solution for your business is one that integrates fully into your existing infrastructure and works within your budget.
How do AI Security Solutions Detect and Prevent Threats?
AI security solutions leverage machine learning algorithms to analyze network traffic, user behavior, and system logs to detect patterns and anomalies associated with known or unknown threats. AI can analyze these threats far faster than human security administrators.
How does AI Help in Incident Response?
AI helps in incident response by automating the analysis of security events, prioritizing alerts based on risk, and providing insights into the root cause of incidents. AI’s strength in incident response is that the system “learns” over time, and so is increasingly effective.
Will AI Replace Human Cybersecurity Professionals?
AI will not replace the field of cybersecurity and related jobs because AI security tools require oversight from IT professionals. However, AI will automate repetitive security tasks and assist security professionals in their work by arming them with AI-based threat detection, investigation, and response.
What is MLSecOps?
MLSecOps, short for Machine Learning Security Operations, is a development and deployment framework for machine learning that considers traditional principles of cybersecurity to improve threat detection and prevention.
Bottom Line: AI Security Software Offers Better Protection
Because today’s threat actors now use AI, it’s imperative that companies of all sizes also use AI to protect against the emergence of AI-based attacks. Fortunately, the AI security software sold by leading vendors is equipped to offer far better protection than legacy security solutions.
When selecting an AI security solution, make sure that the tool’s mix of on-premise, network configurations, and cloud-based software works well with your technology infrastructure, and that the pricing (which may require a sales call to get) fits your budget. Since these AI security companies tend to offer multiple platforms that are complex and wide in scope, it pays to set up several demos before making your choice.
For a deeper understanding of the power of artificial intelligence, read our guide, What is Artificial Intelligence?
The post 10 Best AI Security Tools for 2024: Next-Gen Cyber Solutions appeared first on eWEEK.
Read more here:: www.eweek.com/rss.xml





